OneLogin
OneLogin is a cloud-based identity and access management platform that simplifies secure access to applications through single sign-on (SSO). Integrating OneLogin with Firebolt enhances security and streamlines user authentication for your team.
To integrate OneLogin with Firebolt’s platform, you need to configure both a OneLogin application for Firebolt and Firebolt’s SSO for OneLogin. Detailed instructions can be found in the following sections:
Configure OneLogin application
- In OneLogin, open to the dashboard and select Applications and Add App.
- Search for SAML, and select SAML Test Connector (IdP w/attr).
- Change the Display Name of the app and select Save. This will be the name of the app that will appear in your OneLogin portal.
- Open the SSO tab and copy the value for the SAML 2.0 Endpoint (HTTP). This value will later be used in the Firebolt Configuration step. Note that logout endpoint is not used at this time.
- Select the View Details link at the X.509 Certificate field and copy/download the certificate.
- Navigate to the Configuration tab and fill in the following values:
- Audience - a URI in the following format:
urn:auth0:<tenant_name>:<org_name>-<provider>, where<tenant_name>is app-firebolt-v2,<org_name>is the name of organization, and<provider>is the provider value set in Firebolt configuration step. Example:urn:auth0:app-firebolt-v2:vsko2-onelogin - ACS (Consumer) URL Validator - a valid regular expression. This field is used to ensure OneLogin posts the response to the correct URL, and it validates the ACS URL field.
- ACS (Consumer) URL - the post-back URL for your organization. This is the URL in the following format:
https://id.app.firebolt.io/login/callback?connection=<organization_name>-<provider>&organization=<organization_identifier>. The organization_identifier is needed to select the correct organization during redirects. The authentication flow will fail if this is incorrectly provided or left blank. Example: https://id.app.firebolt.io/login/callback?connection=vsko2-onelogin&organization=org_82u3nzTNQPA8RyoM<organization_name>represents the Organizational name used to create your Firebolt Account. The org name is referenced in your vanity URL.
<provider>represents the provider we’re configuring as our IdP.<organization_identifier>is the unique identifier for your Organization. To retrieve your<organization_identifier>, you can navigate to Configure > SSO in the Firebolt UI, and Click Copy organization SSO identifier.
- Audience - a URI in the following format:
Configure Firebolt for OneLogin
Once your OneLogin application is configured, you can now configure Firebolt to integrate with OneLogin. This can be done using the Firebolt UI, or with SQL.
Integrate with OneLogin using the UI
- To configure the Firebolt SSO integration with OneLogin using the UI, Navigate to Configure > SSO in Firebolt.
-
Enter the following information:
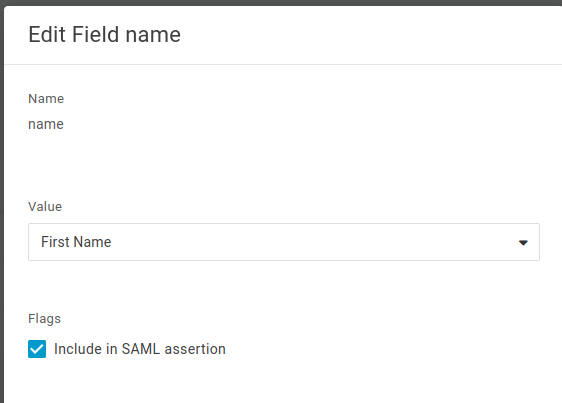
signOnUrl: The sign-on URL, provided by the SAML identity provider, to which Firebolt sends the SAML requests. The URL is IdP-specific and is determined by the identity provider during configuration. In Onelogin, this is the SAML 2.0 Endpoint (HTTP) value we copied in step 4.signoutUrl(optional): The sign-out URL, provided by the application owner, to be used when the user signs out of the application.```issuer: A unique value generated by the SAML identity provider specifying the issuer value.provider: The provider’s name - for example:OneLogin.label: The label to use for the SSO login button. If not provided, the Provider field value is used.certificate: The certificate to verify the communication between the identity provider and Firebolt. The certificate needs to be in PEM or CER format, and can be uploaded from your computer by choosing Import certificate or entered in the text box.field mapping: Mapping to your identity provider’s first and last name in key-value pairs. If additional fields are required, choose Add another key-value pair. Mapping is required for Firebolt to fill in the login’s given and last names the first time the user logs in using SSO.
Here’s an example of how to set up Field mapping:
{ "given_name": "name", "family_name": "surname" }In the previous example:
- given_name (first name) is mapped to the
namefield from the IdP. - family_name (last name) is mapped to the
surnamefield from the IdP.
- Select Update changes.
Integrate with IdP using SQL
To create your SSO connection in Firebolt, you can use the following SQL as an example:
ALTER ORGANIZATION vsko SET SSO = '{
"signOnUrl": "https://vsko-test.onelogin.com/trust/saml2/http-post/sso/aa",
"issuer": "onelogin",
"provider": "onelogin",
"label": "OneLogin Company App",
"fieldMapping": {
"given_name": "name",
"family_name": "surname"
},
"certificate": "<certificate>"
}';
where
organization_nameis the name of the organization in Firebolt,signOnUrlis the SAML 2.0 Endpoint (HTTP) value copied during OneLogin setup,issueris the name of the issuer, ‘onelogin’ in this case,provideris the IdP name, ‘onelogin’ in this case,labelis text that will appear on the Sign in form (this defaults to<organization_name>-<provider>if a value is not provided, for instance ‘acme-onelogin`)certificateis the X.509 Certificate copied during OneLogin setup, andfield_mappingincludes additional fields to be mapped from the SAML assertion, based on what was configured during OneLogin setup. For exaxmple:
{
"given_name": "name",
"family_name": "surname"
}
This corresponds to the following setup in OneLogin, where name/surname in OneLogin corresponds to values in JSON: