- Create a user.
- Create appropriate permissions for this user.
- Create access credentials to authenticate this user.
Create a user
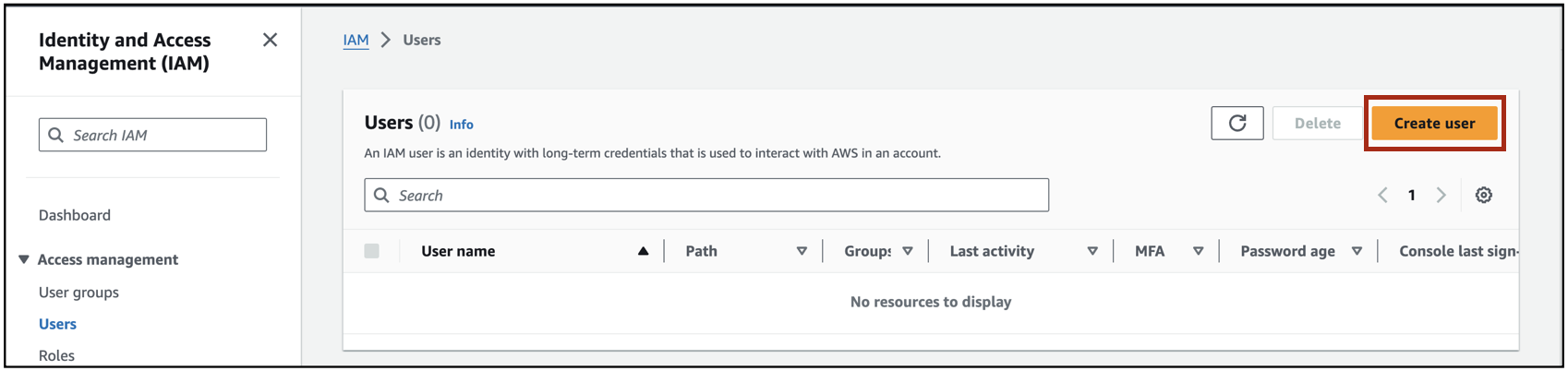
- Log into your AWS Management console and go to the IAM section. You can do this by typing “IAM” in the search bar.
-
Once you are in the IAM section, select the Create User button.
-
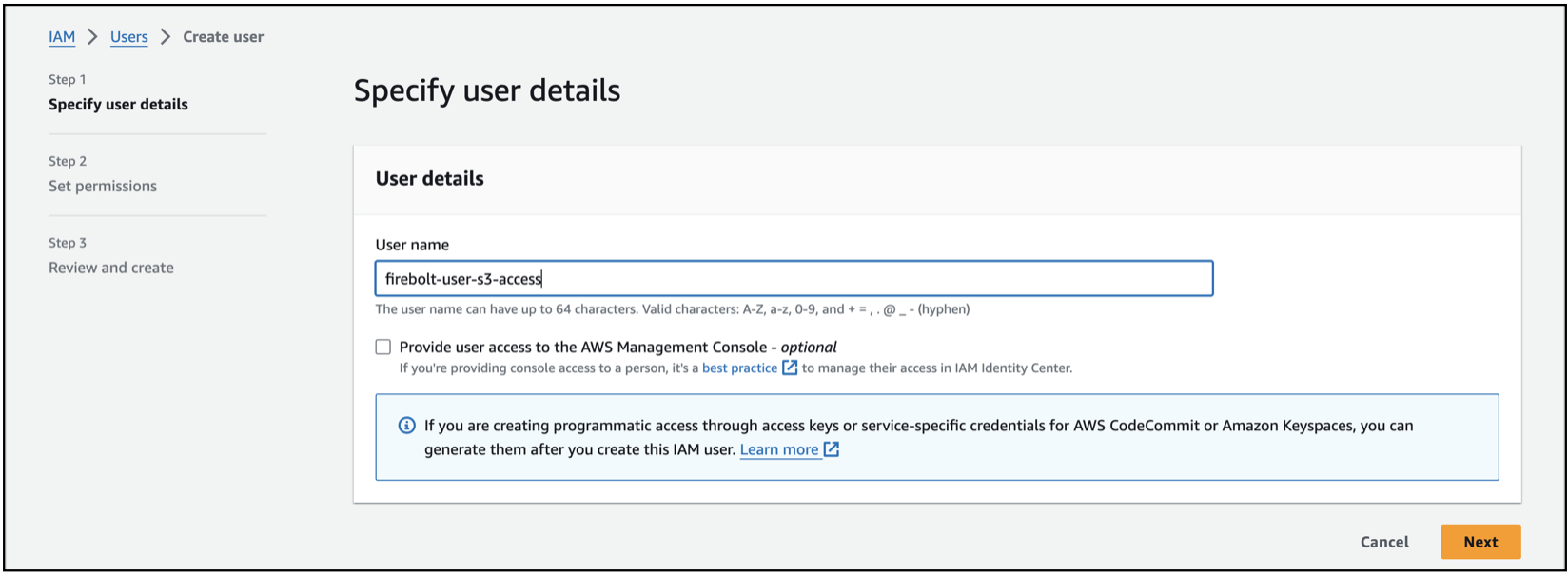
Enter a name for the user and select Next.
-
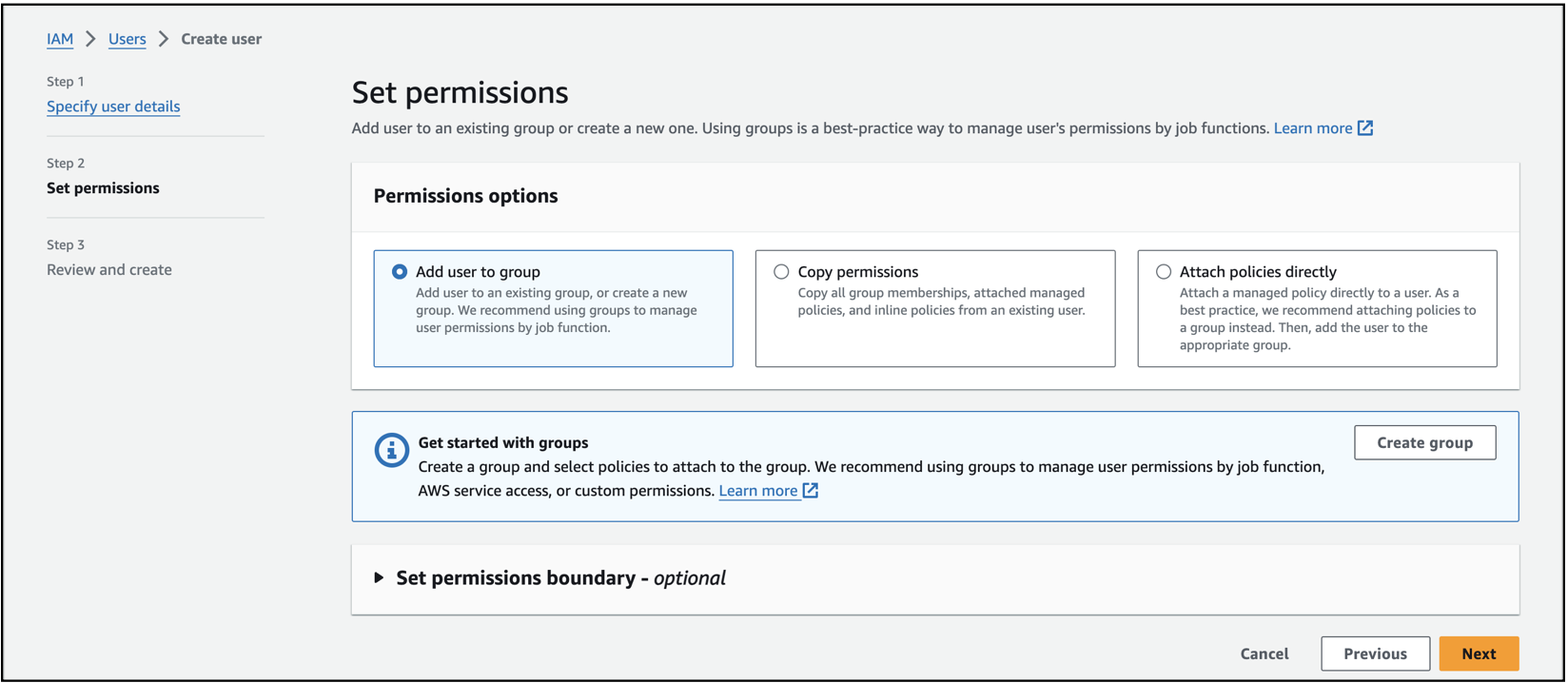
You can have the default permission option set to Add user to group and select Next.
-
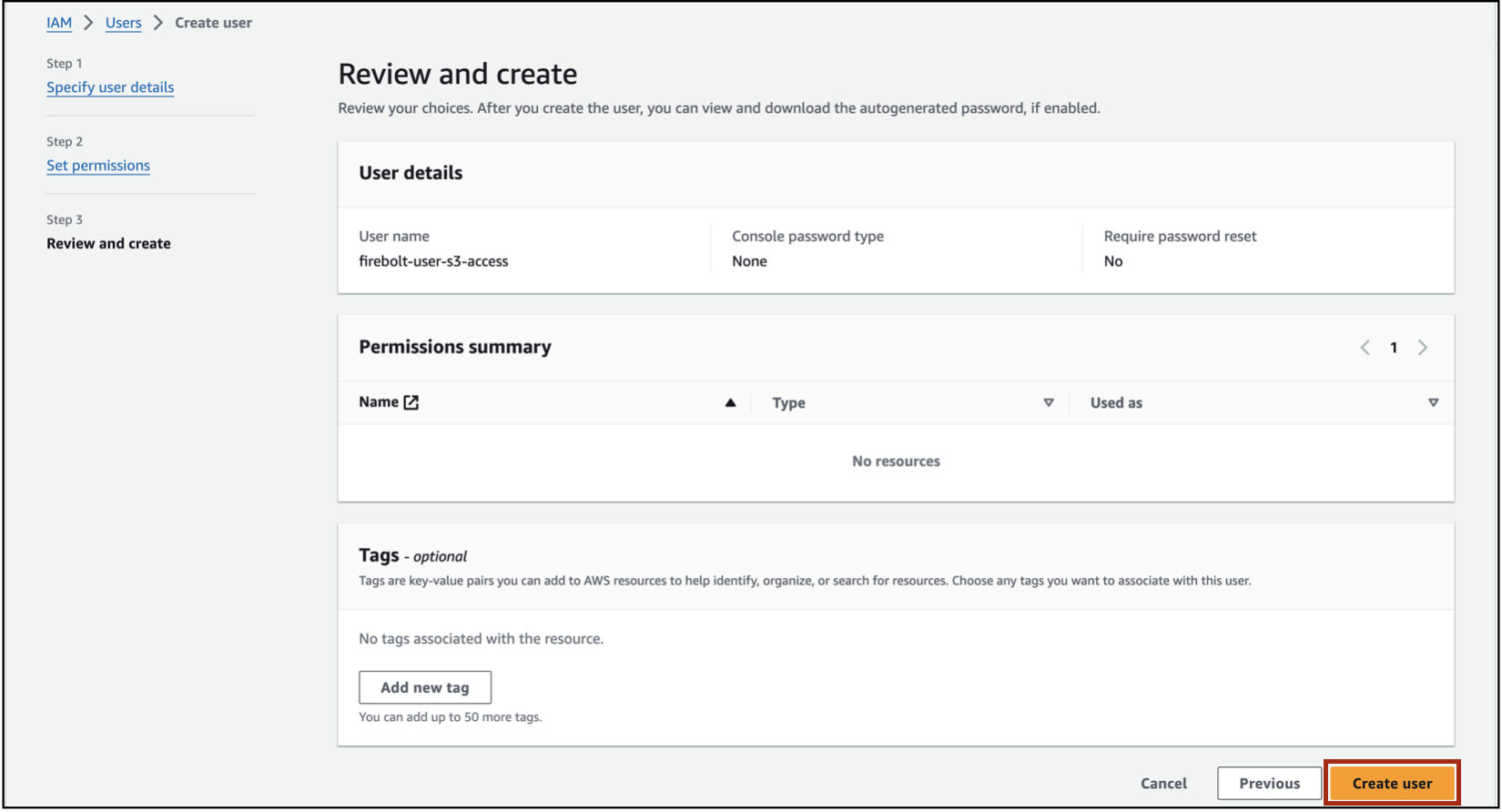
Select Create User.
-
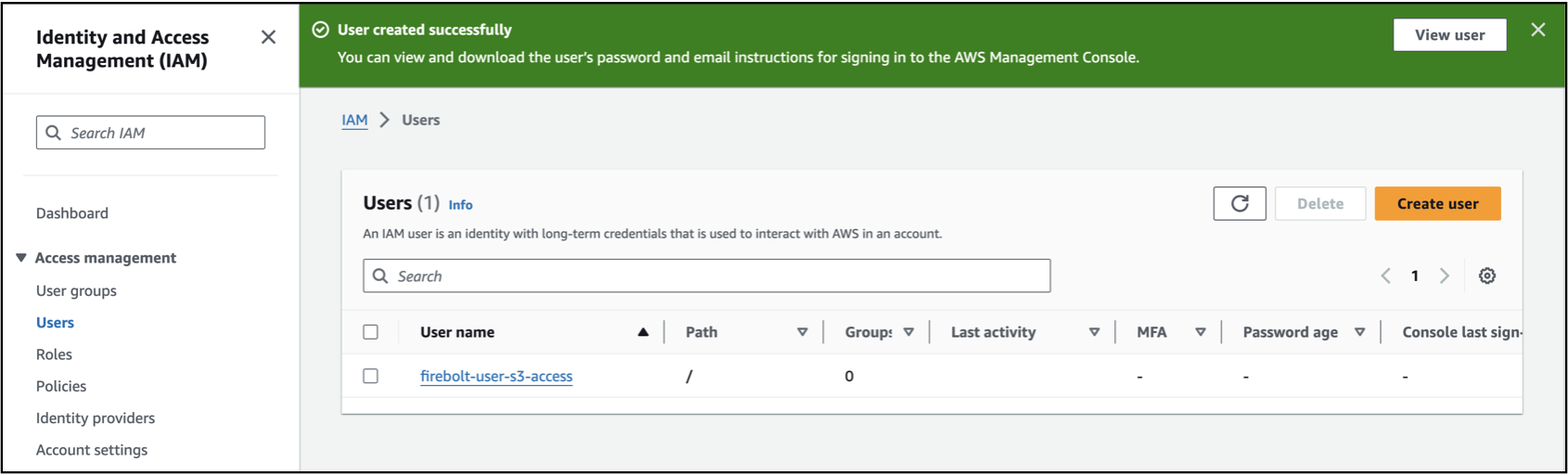
You will see a message User created successfully.
Create S3 access permissions
Now that you have created the user, you will now assign this user appropriate permissions for S3.-
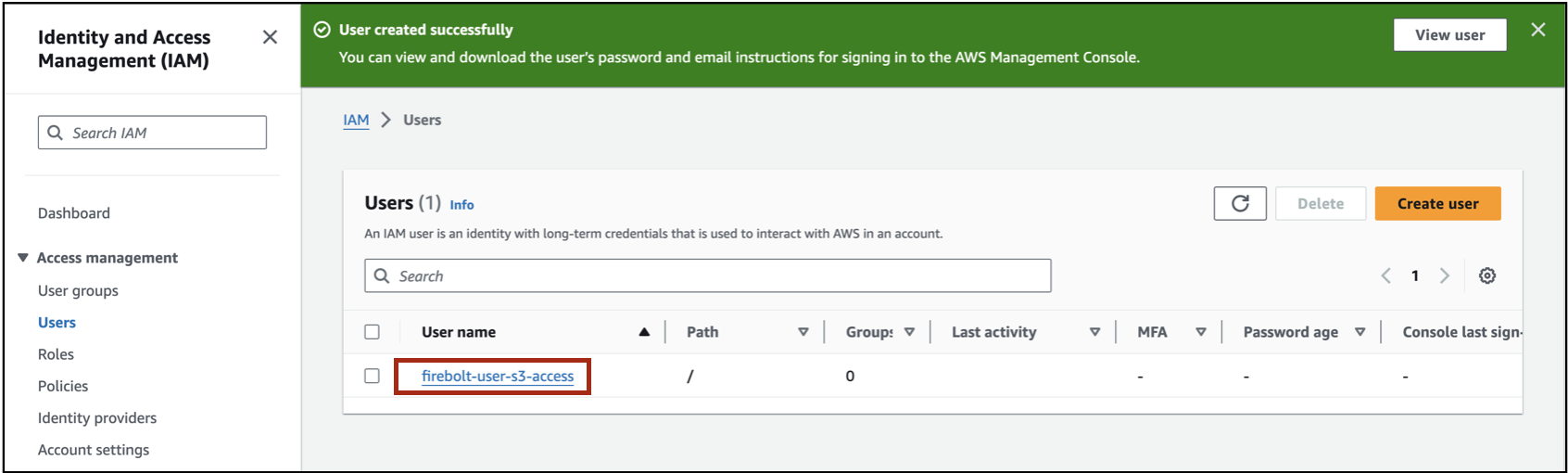
Select on the user name as shown below.
-
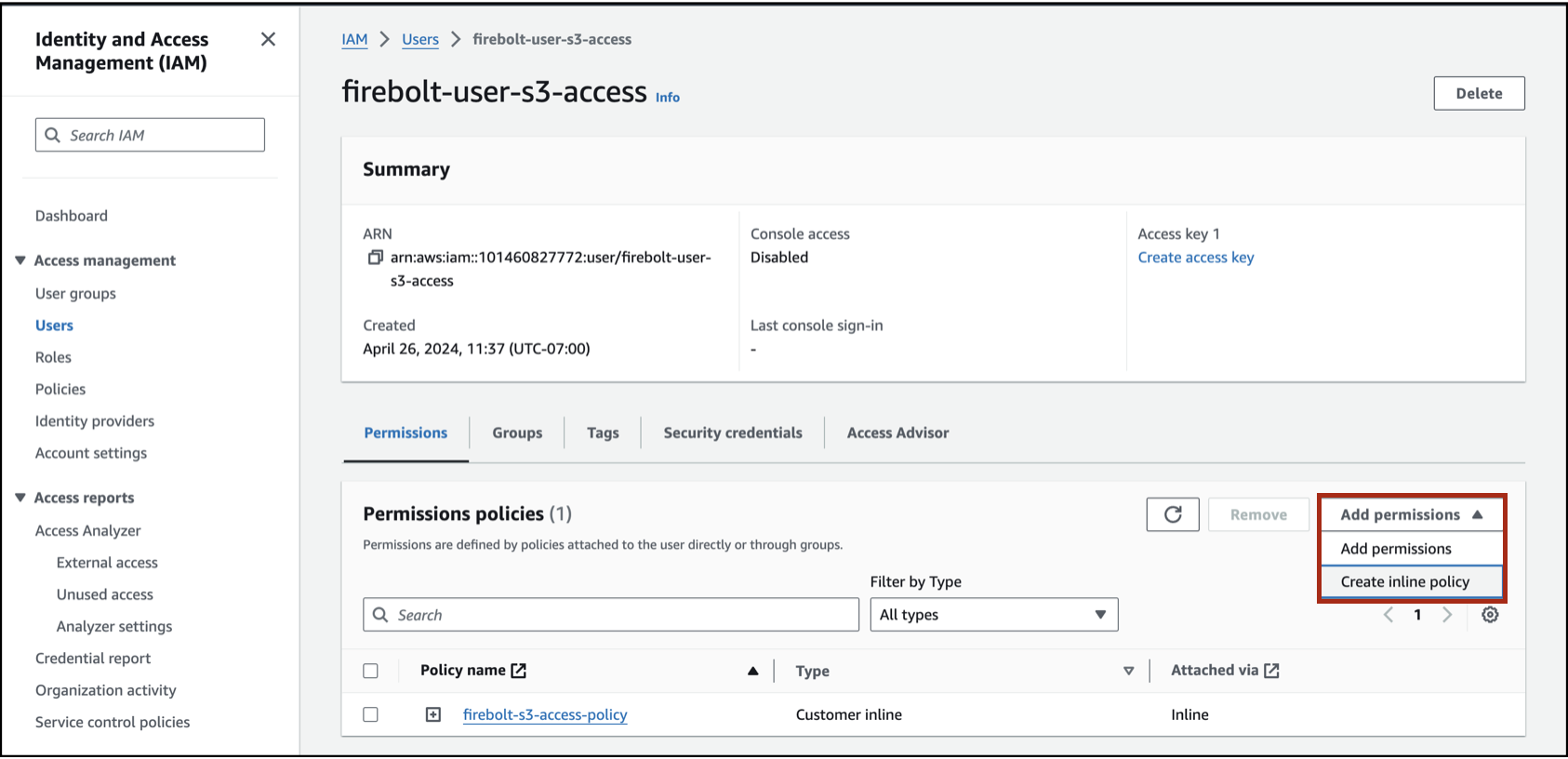
In the Permissions tab, select the Add Permissions drop-down and choose Create inline policy.
-
In Specify Permissions choose S3 as the service.
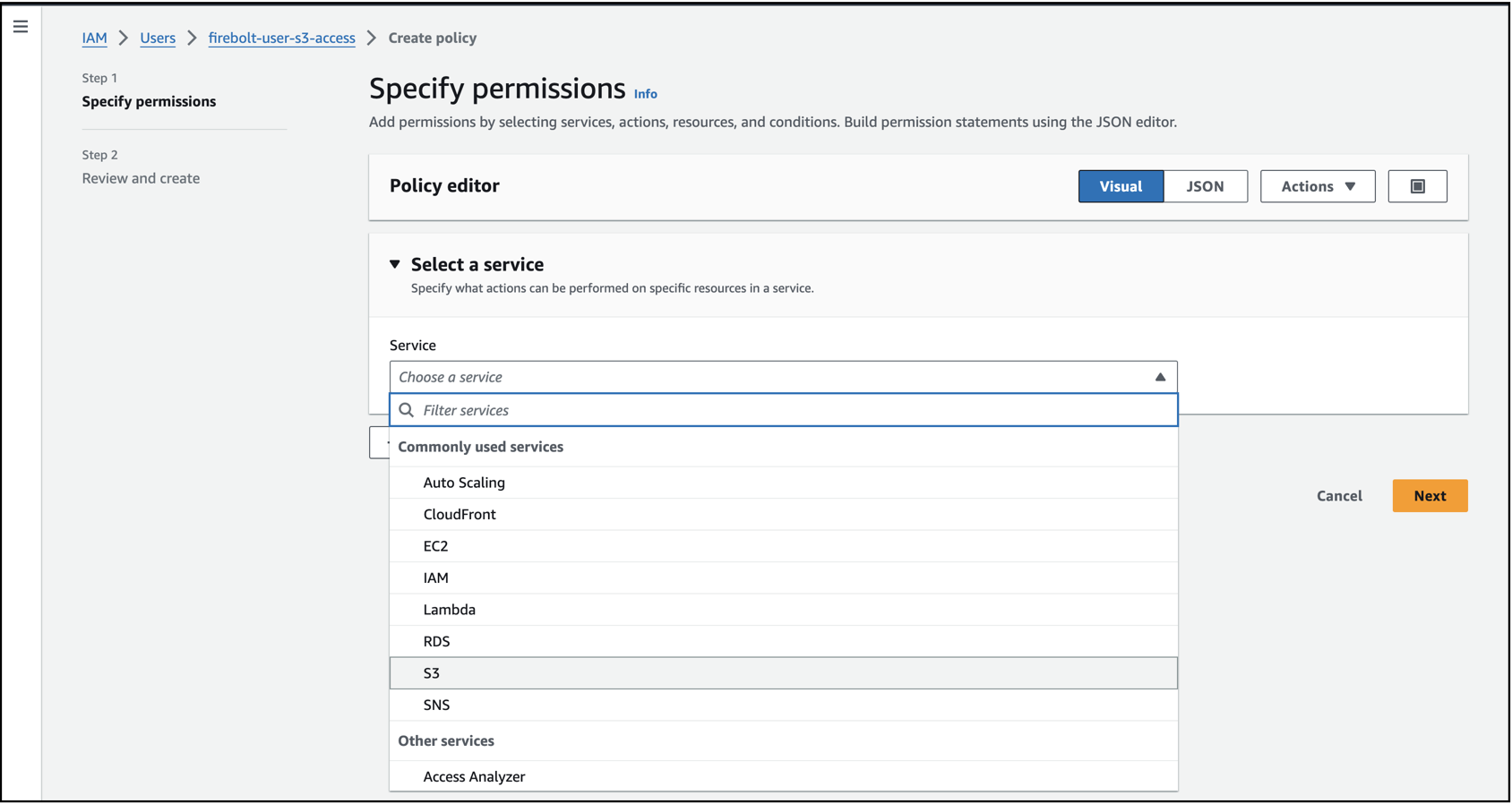
-
Choose JSON, paste the following JSON code in the policy editor, and select Next.
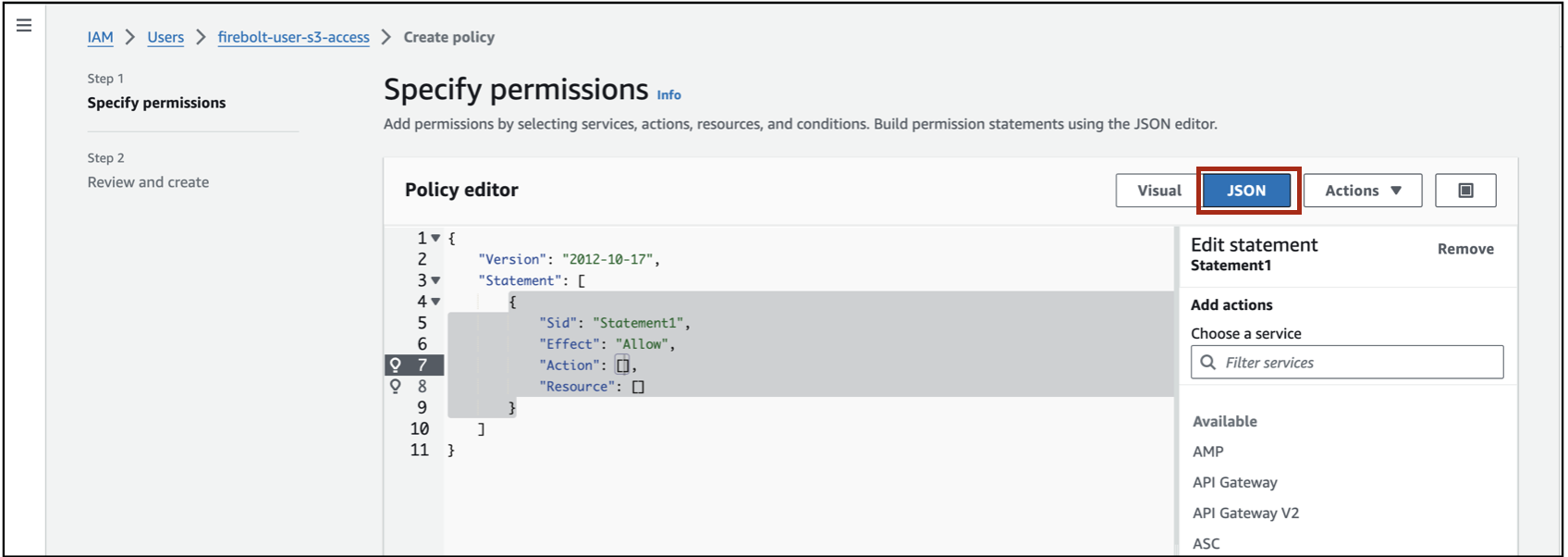
<bucket> with the S3 bucket that you want to provide access to.
-
Enter a description for the policy and select Create Policy.
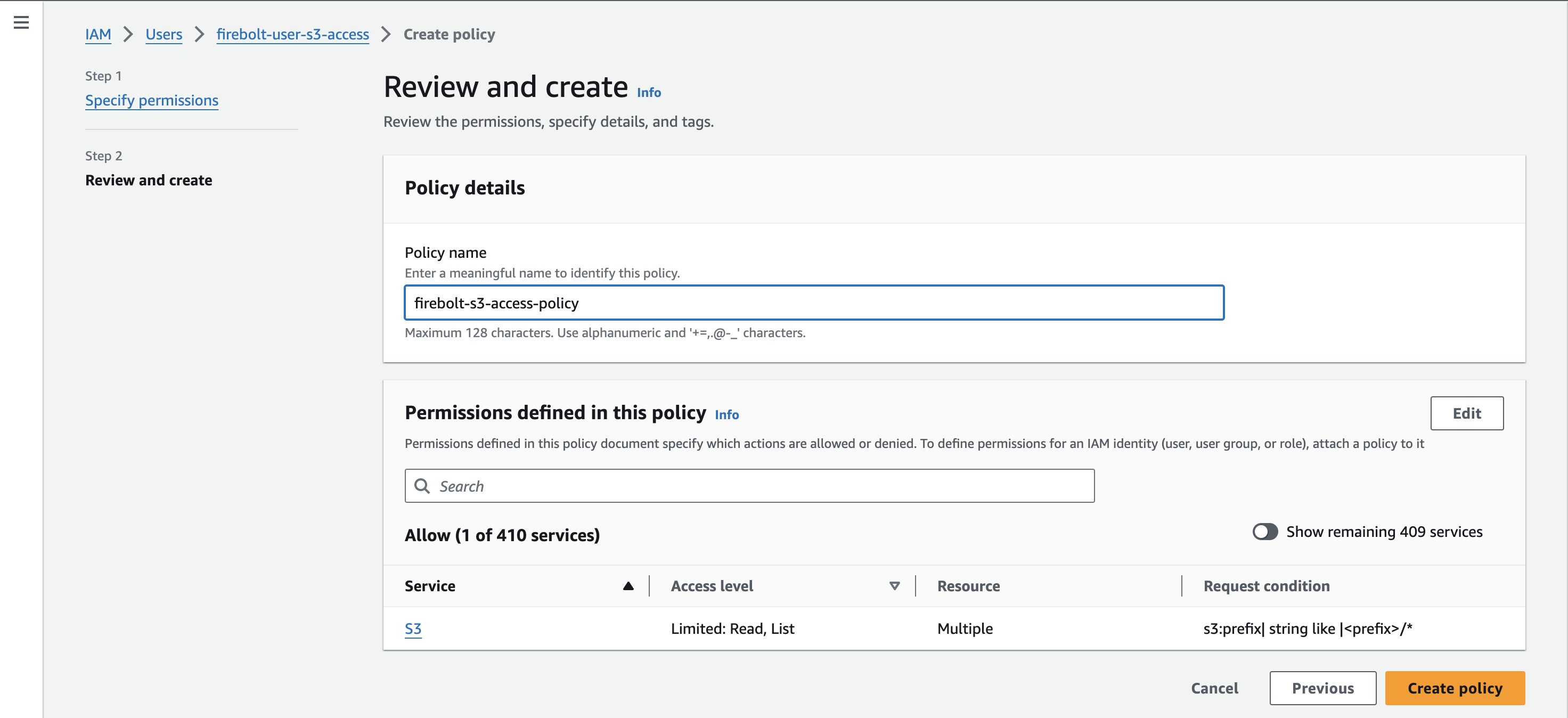
- You will see a message that the policy has been successfully created.
Create access key and secret ID
Now that you have created a user, authorized the user with the appropriate S3 permissions, you will create access credentials for this user. These credentials will be used to authenticate the user.-
Select the Security Credentials tab, as shown in the following image:
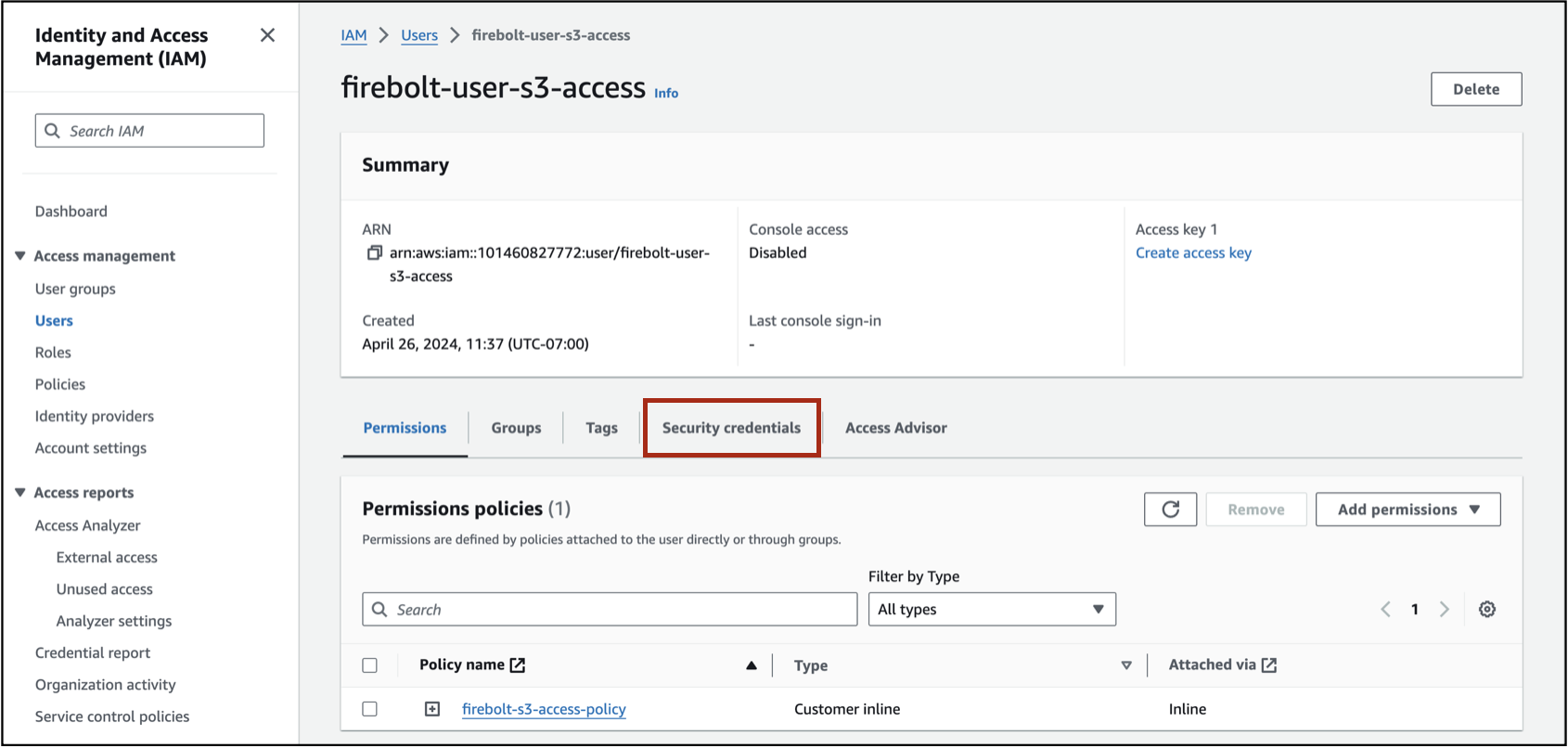
-
In the Access Keys section, select the Create Access Key button.
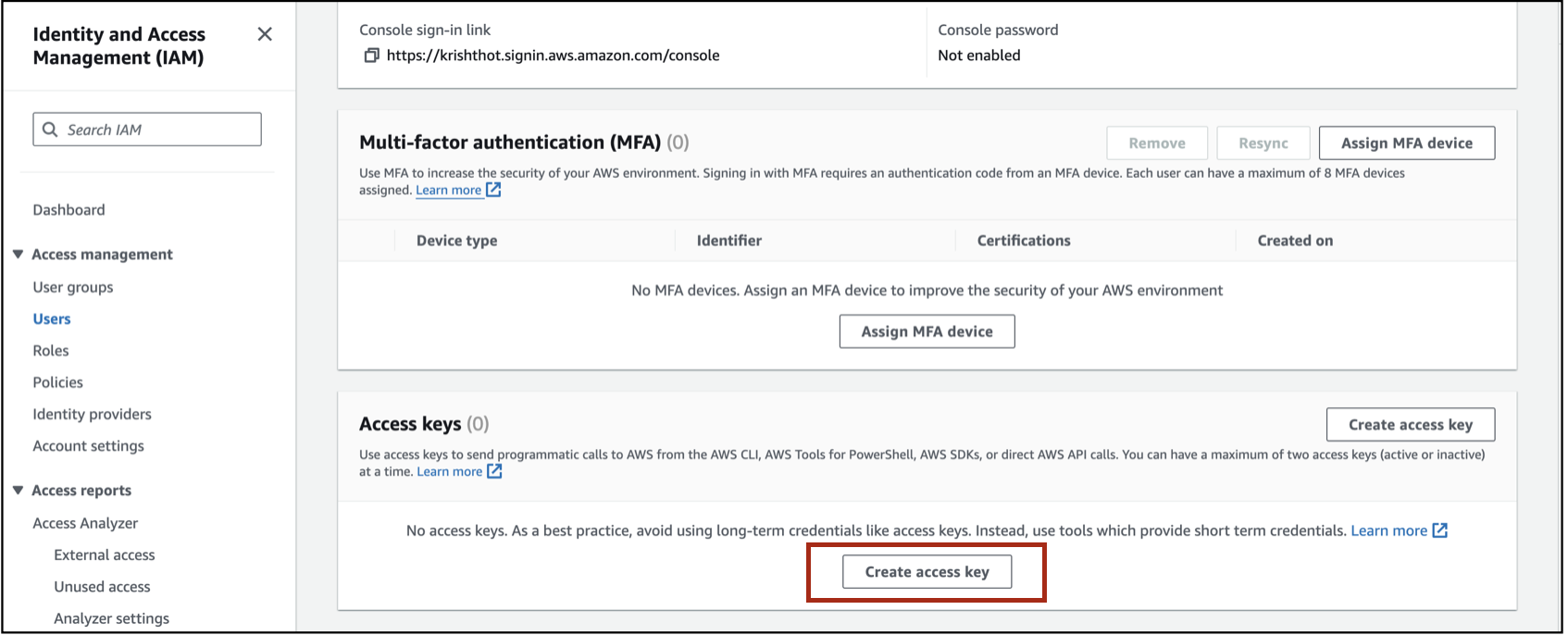
-
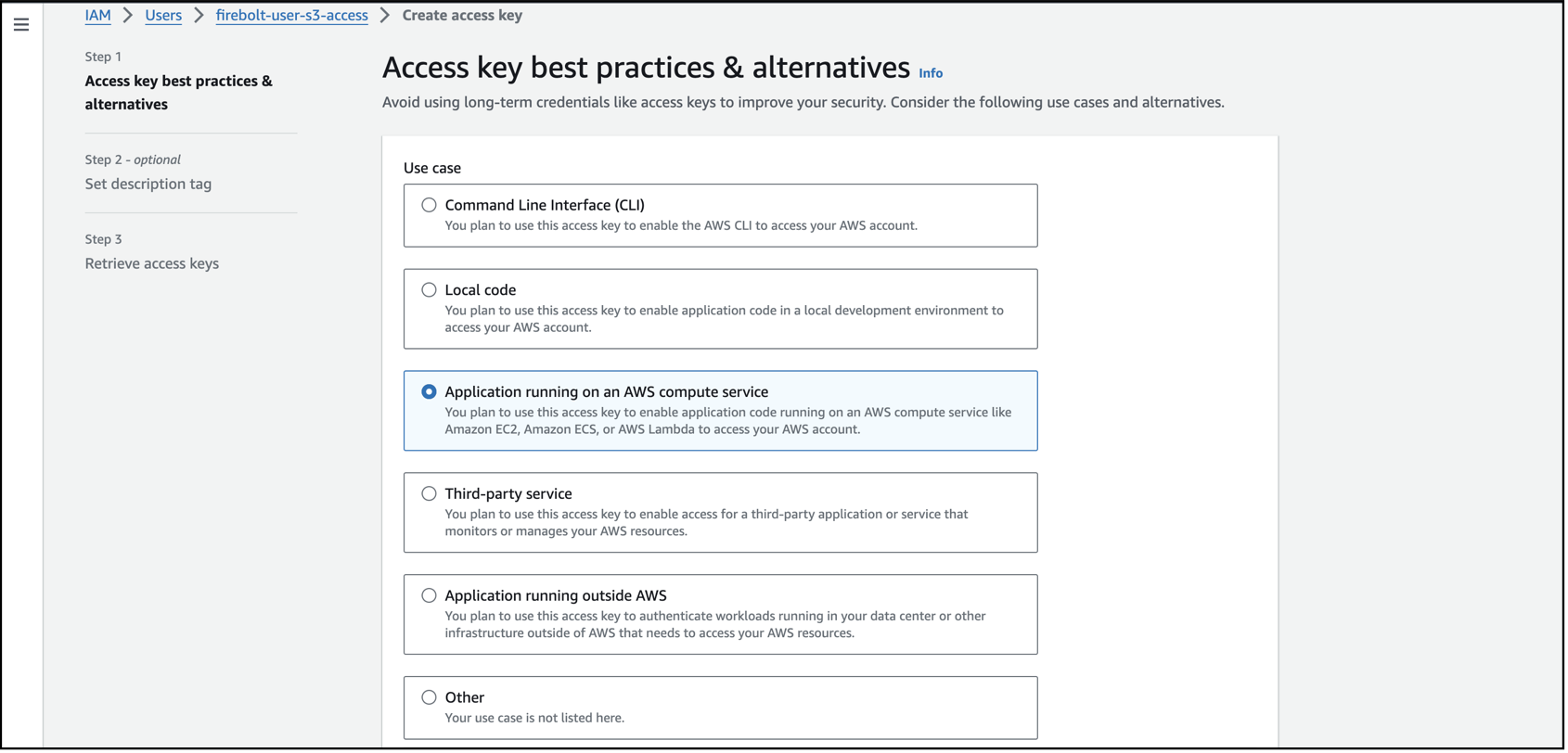
For the use case, choose the Application running on AWS compute service. You will see an alternative recommendation. You can check the box that says “I understand the above recommendation and want to proceed to create an access key” and select Next.
-
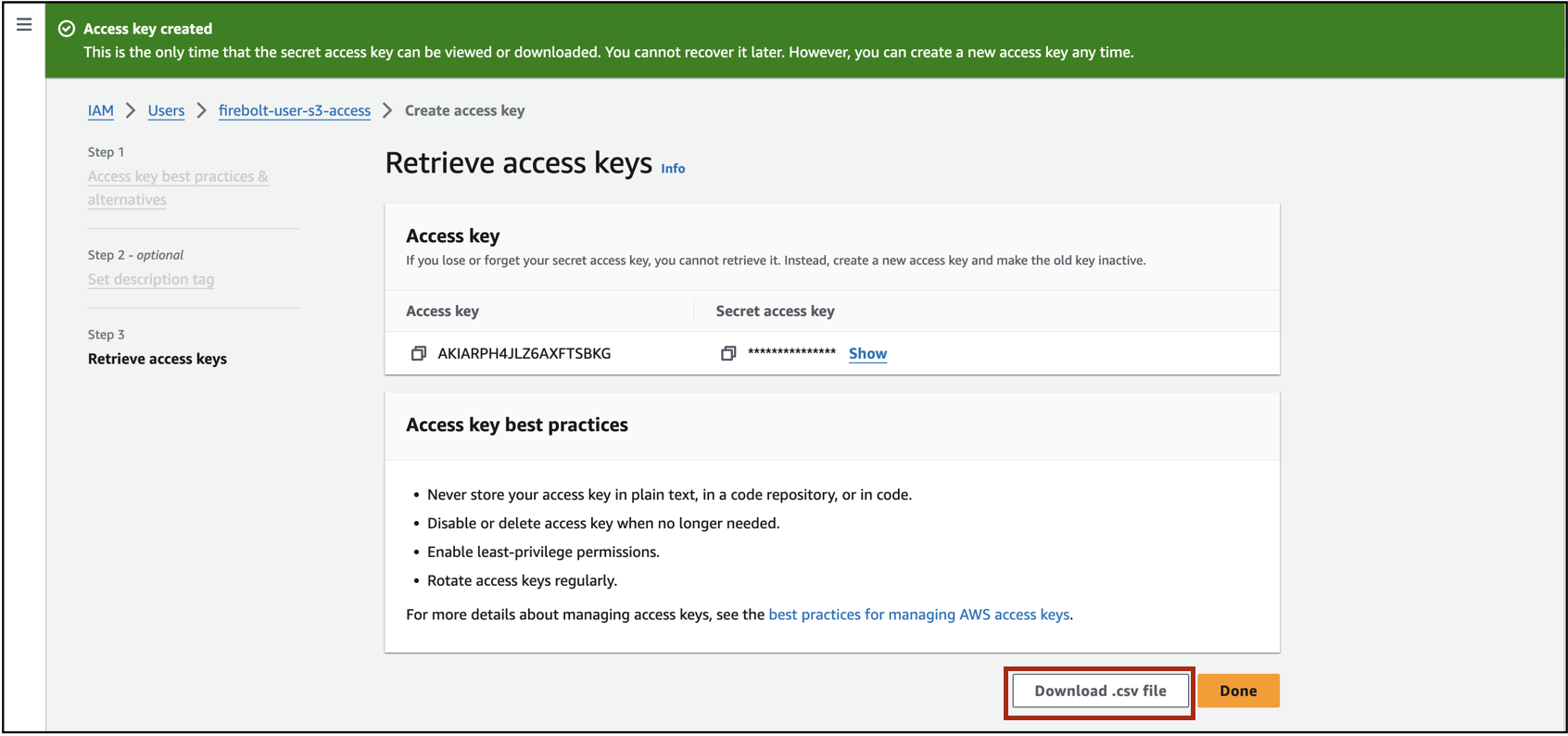
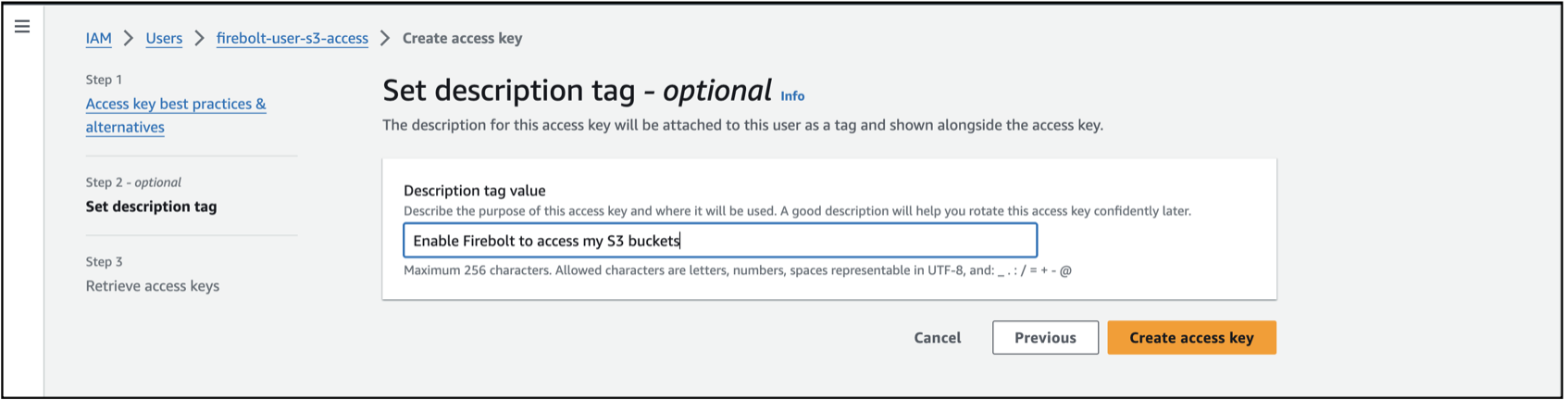
Set a description tag for the access key and select **C,
-
You will see a message indicating that the access key was created. Make sure to download the access key. You will need these credentials when you load S3 data into Firebolt.